GATE Previous Year Wise Questions
gate 2018
GATE 2019
gate 2016
gate 2016 set 1
GATE 2017 SET 1
GATE 2017 SET2
GATE 2015 SET 1
GATE 2015 SET 2
GATE 2015 SET3
GATE 2014 SET 1
GATE 2014 SET 2
GATE 2013
gate 2009
GATE 2012
gate 2010
GATE 2019
GATE 2014 SET 3
gate 2011
GATE 2008 CS
GATE 2008 IT
GATE 2007 CS
GATE 2007 IT
GATE 2006 CS
GATE 2006 IT
GATE 2005 CS
GATE 2005 IT
GATE 2004 CS
GATE Previous Subject Wise Questions
Data Structures
Algorithms
operating systems
computer organization
Computer Networks
DBMS
Graph Theory
Question 41
In an Ethernet local area network, which one of the following statements is TRUE?
A
A station stops to sense the channel once it starts transmitting a frame.
B
The purpose of the jamming signal is to pad the frames that are smaller than the
minimum frame size.
minimum frame size.
C
A station continues to transmit the packet even after the collision is detected.
D
The exponential backoff mechanism reduces the probability of collision on
retransmissions.
retransmissions.
Computer Networks
gate 2016
Question 42
Consider a processor with 64 registers and an instruction set of size twelve. Each instructionhas five distinct fields, namely, opcode, two source register identifiers, one destination register
identifier, and a twelve-bit immediate value. Each instruction must be stored in memory in
a byte-aligned fashion. If a program has 100 instructions, the amount of memory (in bytes)
consumed by the program text is ______________
Submit
computer organization
gate 2016
Question 43
The width of the physical address on a machine is 40 bits. The width of the tag field in a 512KB 8-way set associative cache is ______________ bits.
Submit
computer organization
gate 2016
Question 44
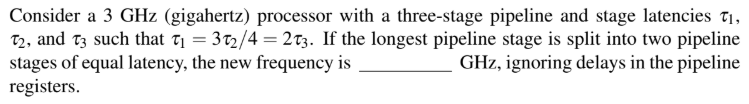
Submit
computer organization
gate 2016
Question 45

Submit
Algorithms
gate 2016
Question 46
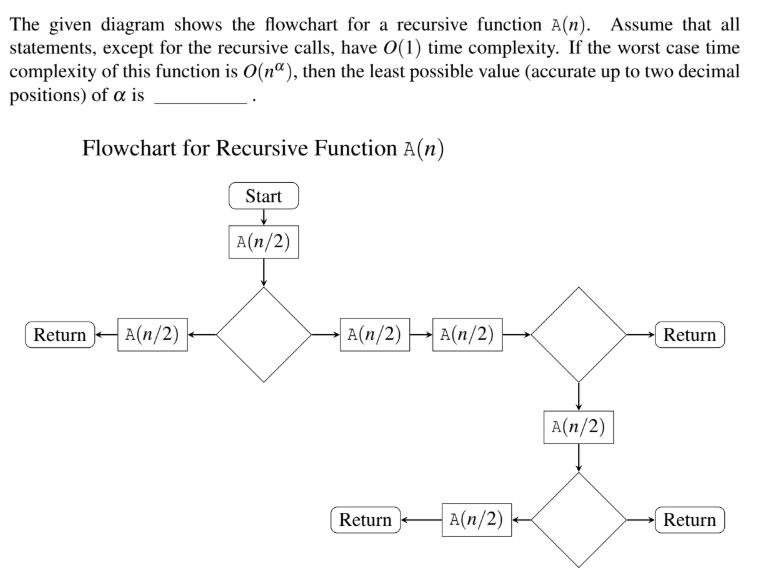
Submit
Algorithms
gate 2016
Time-Complexity
Question 47
The number of ways in which the numbers 1, 2, 3, 4, 5, 6, 7 can be inserted in an empty binarysearch tree, such that the resulting tree has height 6, is __________________
Note: The height of a tree with a single node is 0.
Submit
Data Structures
gate 2016
Question 48

A
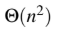
B
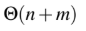
C
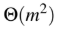
D
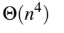
Data Structures
gate 2016
Graphs
Question 49
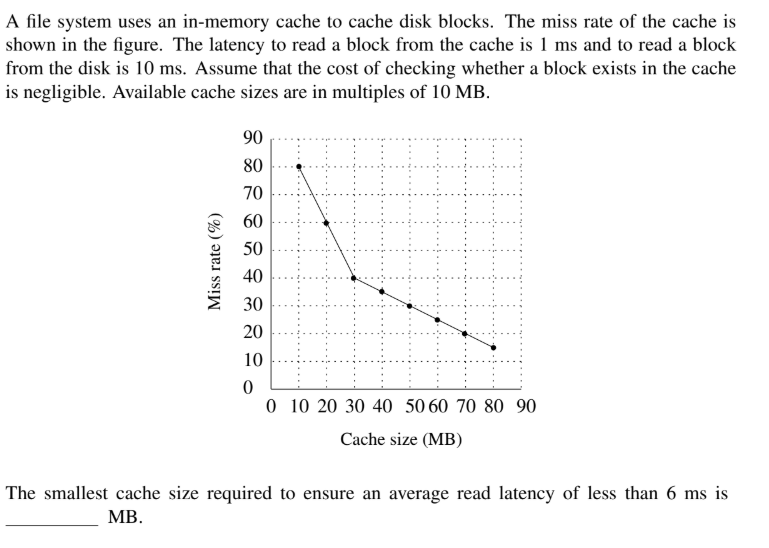
Submit
computer organization
gate 2016
Question 50
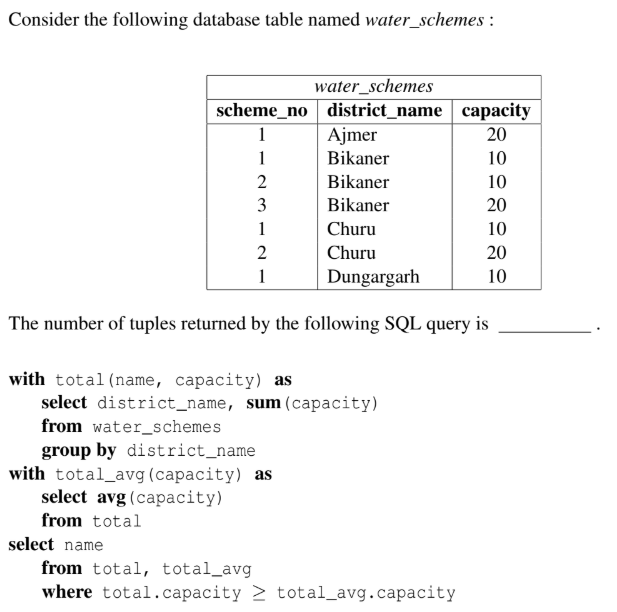
Submit
gate 2016
Question 51

Submit
Computer Networks
gate 2016
Question 52

Note: 802.11 MAC = Wifi
I. This is true, maximum 3 overlapping channels are possible in Wifi.
II. The RTS (Request To Send) and CTS(Clear To Send) are control frames which is used for collision avoidance, not in collision detection, (so, II is False)
III. Every frame in Wifi is Acked, because Wifi stations do not use collusion detection. (True)
I. This is true, maximum 3 overlapping channels are possible in Wifi.
II. The RTS (Request To Send) and CTS(Clear To Send) are control frames which is used for collision avoidance, not in collision detection, (so, II is False)
III. Every frame in Wifi is Acked, because Wifi stations do not use collusion detection. (True)
A
All I, II, and III
B
I and III only
C
II and III only
D
II only
Computer Networks
gate 2016
Question 53

Submit
Computer Networks
gate 2016
Question 54
Consider a TCP client and a TCP server running on two different machines. After completing data transfer, the TCP client calls close to terminate the connection and a FIN segment is sent to the TCP server. Server-side TCP responds by sending an ACK which is received by the client-side TCP. As per the TCP connection state diagram(RFC 793), in which state does the client side TCP connection wait for the FIN from the server-side TCP?
A
LAST-ACK
B
TIME-WAIT
C
FIN-WAIT-1
D
FIN-WAIT-2
Computer Networks
GATE 2017 SET 1
Question 55
A sender S sends a message m to receiver R, which is digitally signed by S with its private key. In this scenario, one or more of the following security violations can take place.(I) S can launch a birthday attack to replace m with a fraudulent message.
(II) A third party attacker can launch a birthday attack to replace m with a fraudulent message.
(III) R can launch a birthday attack to replace m with a fraudulent message.
A
(I) and (II) only
B
(I) only
C
(II) only
D
(II) and (III) only
Computer Networks
GATE 2017 SET 1
Question 56
Let T be a binary search tree with 15 nodes. The minimum and maximum possible heights of T are:Note: The height of a tree with a single node is 0.
A
4 and 15 respectively
B
3 and 14 respectively
C
4 and 14 respectively
D
3 and 15 respectively
Data Structures
GATE 2017 SET 1
Binary-Trees
Question 57
Consider a database that has the relation schema EMP (EmpId, EmpName, and DeptName). An instance of the schema EMP and a SQL query on it are given below.
The output of executing the SQL query is _______. Note: This questions appeared as Numerical Answer Type.
A
1.2
B
2.3
C
2.6
D
3.1
GATE 2017 SET 1
Question 58
Threads of a process share
A
global variables but not heap
B
heap but not global variables
C
neither global variables nor heap
D
both heap and global variables
operating systems
GATE 2017 SET 1
Question 59
Consider a two-level cache hierarchy L1 and L2 caches. An application incurs 1.4 memory accesses per instruction on average. For this application, the miss rate of L1 cache 0.1, the L2 cache experience on average. 7 misses per 1000 instructions. The miss rate of L2 expressed correct to two decimal places is ______________.
Submit
computer organization
GATE 2017 SET 1
Question 60
Consider the following functions from positives integers to real numbers 10, √n, n, log2n, 100/n. The CORRECT arrangement of the above functions in increasing order of asymptotic complexity is:
A
log2n, 100/n, 10, √n, n
B
100/n, 10, log2n, √n, n
C
10, 100/n ,√n, log2n, n
D
100/n, log2n, 10 ,√n, n
Algorithms
GATE 2017 SET 1
© 2026 - All rights are reserved- AAIC Technologies pvt ltd

